25+ network diagram examples with ip addresses
The syslog process was one such system that has been widely accepted in many operating systems. ASCII characters only characters found on a standard US keyboard.
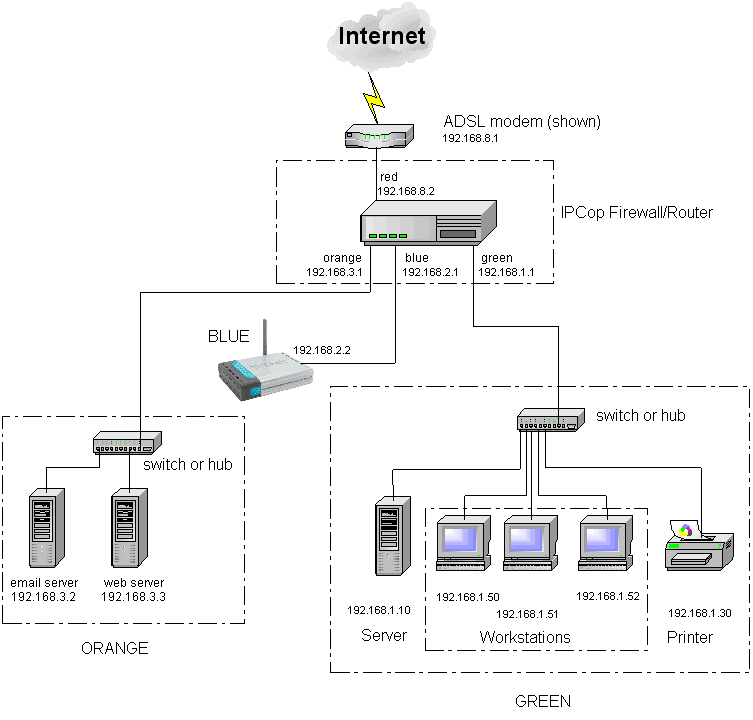
Guard Your Network With Ipcop Part 1 Installation Basics Open Source For You
The scheme did a method identifier and a unique method-specific identifier specified by the DID method.

. Network diagrams are often drawn with professional drawing software tools. Flexibility was designed into this process so the operations staff have the ability to configure the destination of messages sent from the processes running on the. Cloud computing is the on-demand availability of computer system resources especially data storage cloud storage and computing power without direct active management by the user.
BitTorrent is a communication protocol for peer-to-peer file sharing P2P which enables users to distribute data and electronic files over the Internet in a decentralized manner. Peripheral Component Interconnect PCI is a local computer bus for attaching hardware devices in a computer and is part of the PCI Local Bus standard. On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined the.
HTML XHTML XML CSS JavaScript 1158. DIDs are resolvable to DID documentsA DID URL extends the syntax of a basic DID to incorporate other standard URI components such as path query and fragment in order to. For example if the kubelet being restarted with the new set of --node-labels but the same Node name is used the change will not take an effect as labels are being set on the Node registration.
One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967. RFC 3164 The BSD syslog Protocol August 2001 differentiate the notifications of problems from simple status messages. The two IP addresses that you use in the neighbor command of the peer routers must be able to reach one another.
To send or receive files users use a BitTorrent client on their Internet-connected computerA BitTorrent client is a computer program that implements the BitTorrent protocol. IPv4 was the first version deployed for production on SATNET in 1982 and on the ARPANET in January 1983. The host property is not needed when.
Large clouds often have functions distributed over multiple locations each location being a data centerCloud computing relies on sharing of resources to achieve coherence and typically. Whirlpool Refrigerator Led Lights Flashing. In a logical network diagram you can see elements such as routing domains network objects firewalls and routers subnets VLAND IDs IP addresses subnet mask voice gateways and specific routing protocols network segments and traffic flow.
How the Web Works 636 Web Page Design and Programming Languages. Packet switching allows delivery of variable bit rate data streams realized as sequences of. The PCI bus supports the functions found on a processor bus but in a standardized format that is independent of any given processors native bus.
The host property is required for any remote connection and can be either the hostname or IP address v4 or v6 of the endpoint to be assessed. Look at some route map examples. Custom network diagram Visualize and keep track of.
Devices connected to the PCI bus appear to a bus master to be. In computing a denial-of-service attack DoS attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a networkDenial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an. For IPv6 use mask 128.
To add the public IP addresses for each site use the New-CsTenantTrustedIPAddress cmdlet. These IP addresses are in the 1302110022 and 351910016 ranges. DIDs and DID URLs A Decentralized Identifier or DID is a URI composed of three parts.
The ip default-network command. Must contain at least 4 different symbols. To ensure that all Wikipedia content is verifiable Wikipedia provides a means for anyone to question an uncited claimIf your work has been tagged please provide a reliable source for the statement and discuss if needed.
It is one of the core protocols of standards-based internetworking methods in the Internet and other packet-switched networks. The type property MUST be configured to one of the connection types specified above local ssh windows ios panos. Azure Stack Hub uses a total of 31 addresses from this network and the rest are used by tenant VMs.
You can add a citation by selecting from the drop-down menu at the top of the editing boxIn markup you can add a citation manually using ref tags. As mentioned in the Node name uniqueness section when Node configuration needs to be updated it is a good practice to re-register the node with the API server. The network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or more generally any telecommunications network.
A logical network diagram shows how data and information flow in a network. The remaining 16 IPs are reserved for future Azure services. Simple Network Management Protocol 251 Introduction 252 Protocol 253 Structure of Management Information 254 Object Identifiers 255 Introduction to the Management Information Base 256 Instance Identification 257 Simple Examples 258 Management Information Base Continued 259 Additional Examples 2510 Traps 2511 ASN1.
We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. BitTorrent clients are available for. For IPv4 use mask 32.
There are different types of network diagrams provided by EdrawMax and you can get started with it now. If the external IPs seen by Microsoft 365 are both IPv4 and IPv6 addresses you need to add both types of IP addresses. PRTG filters traffic by IP addresses PRTG displays IP data on custom dashboards PRTG sounds the alarm in the event of IP anomalies.
You can define an unlimited number of trusted IP addresses for a tenant. The standard and amendments provide the basis for wireless network products using the Wi-Fi brand and are. IP Addresses URLs ISPs DNS ARPANET 847 World Wide Web.
The routing and transferring of data by means of addressed packets so that a channel is occupied during the transmission of the packet only and upon completion of the transmission the channel is made available for the transfer of other traffic. Examples include 1234 or CIS-CAT-TEST. Also network 20020000 is the choice for the candidate default.
A simple definition of packet switching is. It is still used to route most Internet traffic today even with the. Get 247 customer support help when you place a homework help service order with us.
One way to verify reachability is an extended ping between the two IP addresses. The IP address of the Google Front End GFE that connected to the backend. IEEE 80211 is part of the IEEE 802 set of local area network LAN technical standards and specifies the set of media access control MAC and physical layer PHY protocols for implementing wireless local area network WLAN computer communication.
Case Studies Customer success stories. After switching to LEDs or when replacing a faulty LED lamp in some cases the LED light will start flickering We will explain temperature settings alarm sounds door not closing water filter changes not cooling issues not making ice no power strange sounds leveling ice makers water dispensers This refrigerator has the. 6 to 30 characters long.
Internet Protocol version 4 IPv4 is the fourth version of the Internet Protocol IP. If you plan to use App Service and the SQL resource providers 7 more addresses are used. From the 31 addresses 8 public IP addresses are used for a small set of Azure Stack Hub services.
About Us 25 years of experience. When running HTTP reverse proxy software on the load balancers backends the software might append one or both of the following IP addresses to the end of the X-Forwarded-For header.
How To Change My Ip Address So I Don T Get Flagged Signing Up For A Website Quora

Network Topology Is The Arrangement Of The Various Elements Links Nodes Etc Of A Communication Network Network Topology Communication Networks Networking
If A Mac Address Is Burnt Onto A Device Unique How Come There Are Multicast Mac Addresses Does It Mean This Multicast Address Changes The Unicast Address That Uniquely Identifies My

November 2019 Nikica Varadi

Network Diagram Examples Diagram Design Network Infrastructure Visio Network Diagram
Network Diagram Project Management With Examples Staragile

23 Simple Computer Network Diagram For You Http Bookingritzcarlton Info 23 Simple Computer Network Di Computer Network Networking Basics Wireless Networking

Address Resolution Protocol Types Differences Its Applications
Is 123 132 212 32 A Valid Ip Address Quora

Mitel Clearspan Topology Cisco Networking Networking

Isometric Network Diagram By Bobby Hodges Diagram Design Visio Network Diagram Small Business Network

Network Location Diagram Online Networking Cctv Security Systems Networking
Solved May I Get Explanation For The Below Course Hero
2
Is There Any Problem With Connecting Two Routers To The Same Network With The Same Network Name Quora
Why Does My Wifi Have 3 Ip Addresses Quora
How To Check A Gateway Ip Address Quora